Whenever you read something about security and passwords, there is often the suggestion to use multi factor authentication, for example with one time passwords (OTP). I activate MFA and OTPs whenever available. It’s pretty easy to implement them with Solaris 11.4 as well. So you use OTP in addition to your normal passwords.
How to configure OTP
At first: Please ensure that the device that is generating the OTP and the system yu want to use them have a common time base. The OTP in this example are time based and while the mechanism allow for some variances - you don’t need PTP - however they should be reasonably close.
You have to execute commands with root privileges as well as the user that will use OTP. So please look at the beginning of the command lines which user is the correct one for the step.
At first you must install OTP on your system with a suffiently privileged user. I will use root for this task. At first you have to install the otp package.
root@testbed:~# pkg install otp
Packages to install: 1
Create boot environment: No
Create backup boot environment: No
DOWNLOAD PKGS FILES XFER (MB) SPEED
Completed 1/1 15/15 0.1/0.1 58.2k/s
PHASE ITEMS
Installing new actions 30/30
Updating package state database Done
Updating package cache 0/0
Updating image state Done
Creating fast lookup database Done
Updating package cache 1/1
root@testbed:~#Now I would like to suggest to check - especially when you are working in a playground system in a VM - if the clock of your computer is reasonably correct.
root@testbed:~# ntpdate ntp1.ptb.de
8 Jun 09:20:10 ntpdate[954]: adjust time server 192.53.103.108 offset -0.171305 secIt’s important, that you set up OTP for at least one user (one that is able to assume root privileges) before configuring PAM and ssh for OTP. Even better: Install the tool like described before and then tell every user that she or he should set up their OTP accordingly and report this back to you. When everyone has completed this step, you should switch OTP on. As soon, as you change the ssh and PAM configuration, people won’t be able to log into the system as they don’t have OTP.
So i’m changing to a shell of the one demo user on my VM. It’s the user jmoekamp. To set up your authenticator app, you need a secret, “seeding” the calculation of the OTP codes.
jmoekamp@testbed:~$ otpadm set secret
New TOTP secret=PRUC JQJV FAB2 XEBV 4DKS 5BGU AXTT VLJFI will use the Google Authenticator in my tutorial, because because i’m not using it normally, so the screenshots won’t contain other accounts.
At first you have to use the TOTP secret and configure the account. Type in the secret. Account name doesn’t matter, as long as you know what it is.
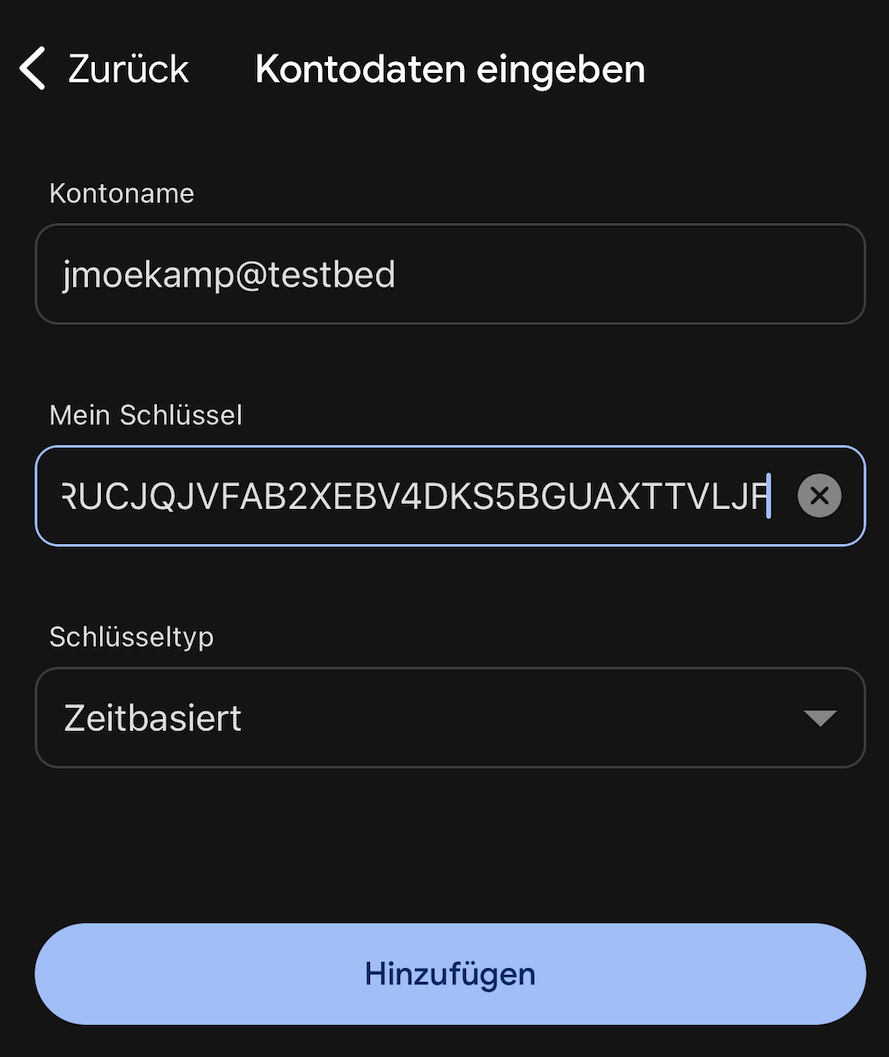
The system checks, if you put in the secret correctrly into your authentication app, by asking you for an OTP code generated with this very secret. If the OTP code is correct, the system knows you didn’t made an error at this point.
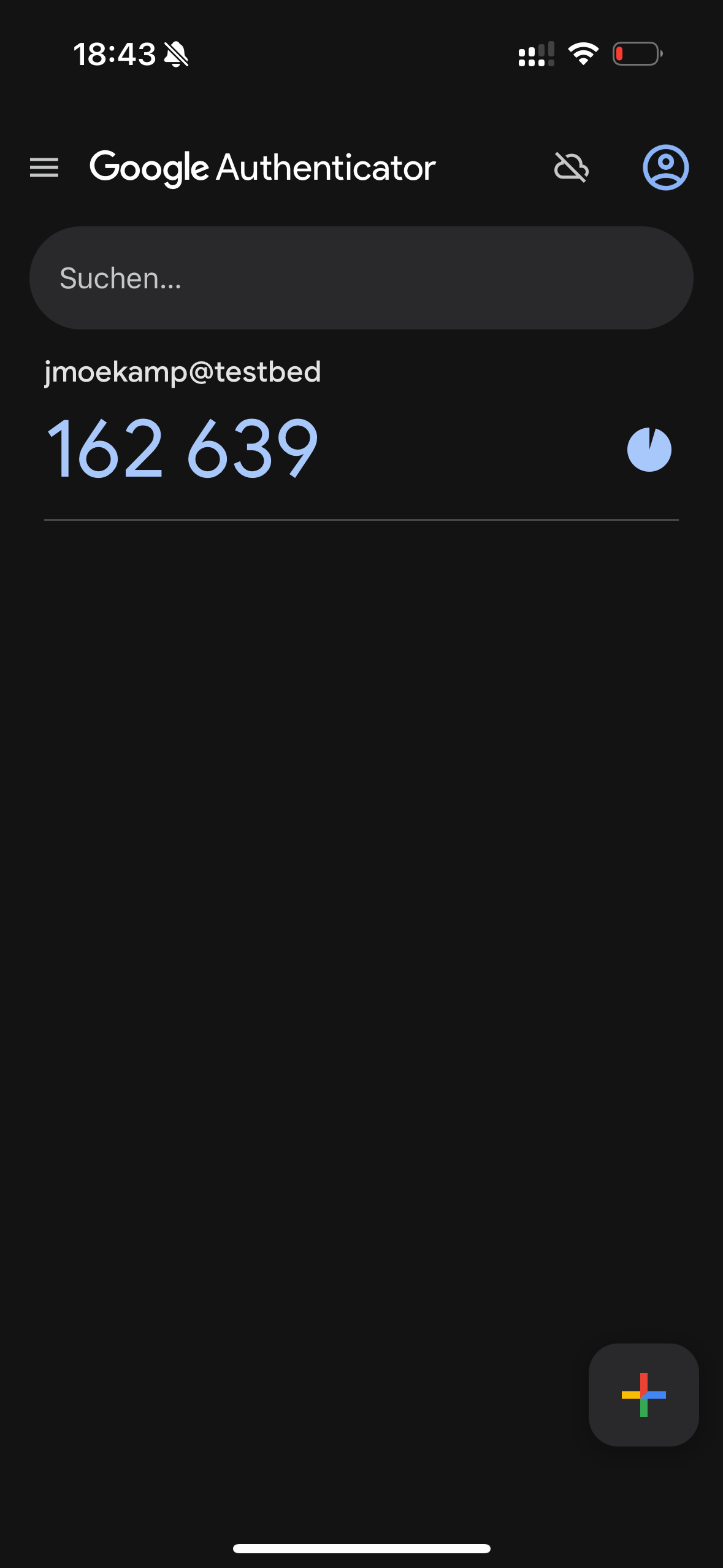
Just put it into the line asking for the code from authenticator:
jmoekamp@testbed:~$ otpadm set secret
New TOTP secret=PRUC JQJV FAB2 XEBV 4DKS 5BGU AXTT VLJF
Enter current code from authenticator: 162639For a basic configuration, that’s all. All users on your system have to repeat this.
Configuring ssh and PAM
Back to the root shell. Now we are configuring OTP for SSH.
At first i will check, if someone has already configured AuthenticationMethods in the /etc/ssh/sshd_config file. You should also check in any file residing in /etc/ssh/sshd_config.d/.
root@testbed:~# grep "AuthenticationMethods" /etc/ssh/sshd_configIf there is already such a line, you have to merge your existing configuration with the configuration i will describe in the next step.
Now i’m changing AuthenticationMethods to password,keyboard-interactive. So either a valid key or password and the one time password will allow you to access the account. You won’t be able to use public key authentication with this configuration. I will change this later.
root@testbed:~# echo "AuthenticationMethods password,keyboard-interactive" > /etc/ssh/sshd_config.d/otp.confNow we have to configure the sshd-kbdint PAM service used by the keyboard-interactive authentication method.
root@testbed:~# echo "auth required pam_unix_cred.so.1" > /etc/pam.d/sshd-kbdint
root@testbed:~# echo "auth required pam_otp_auth.so.1" >> /etc/pam.d/sshd-kbdint
root@testbed:~# cat /etc/pam.d/sshd-kbdint
auth required pam_unix_cred.so.1
auth required pam_otp_auth.so.1Now i’m restarting the ssh service.
root@testbed:~# svcadm restart ssh; sleep 10; svcs -x ssh
svc:/network/ssh:default (SSH server)
State: online since 2025-06-08T09:33:12
See: sshd(8)
See: /var/svc/log/network-ssh:default.log
Impact: None.Okay, it’s done . OTP for SSH should work now.
First test
Let’s try the first ssh login with OTP enabled. Get into your OTP app and have your 6 digit code ready:
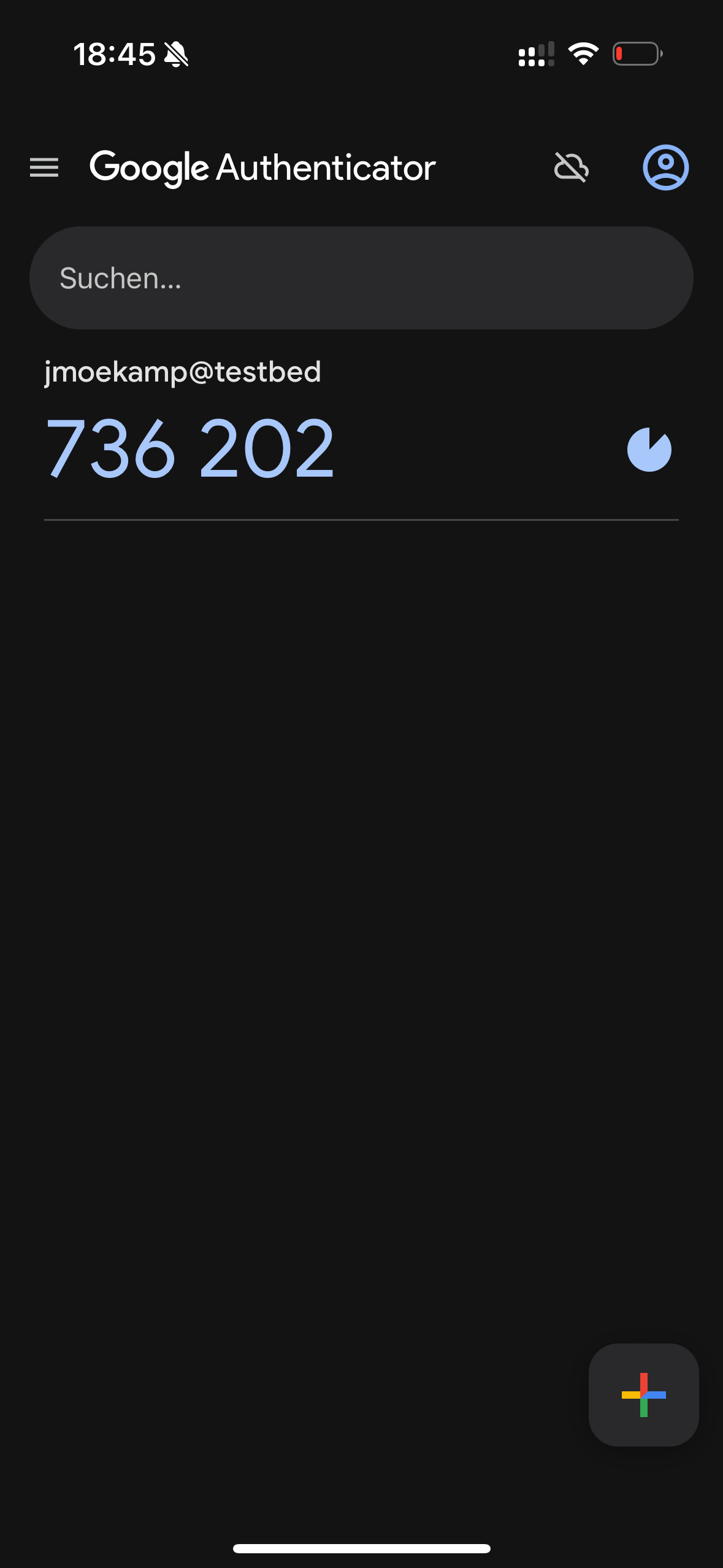
Put this code into the “OTP code” line.
joergmoellenkamp@Mac ~ % ssh jmoekamp@192.168.99.99
jmoekamp@192.168.99.99's password: supersecret
(jmoekamp@192.168.99.99) OTP code: 736202
Last login: Sun Jun 8 16:42:47 2025 from 192.168.98.99
Oracle Solaris 11.4.81.195.2 Assembled May 2025It worked.
Password-less
Of course you could still use passwordless authentication without OTP, while enforcing OTP usage with normal password.
root@testbed:~# echo "AuthenticationMethods publickey password,keyboard-interactive" > /etc/ssh/sshd_config.d/otp.conf
root@testbed:~# svcadm restart sshdNow you don’t need a password given you have deployed your public key on the accounts authorized_keys.
joergmoellenkamp@Mac ~ % ssh jmoekamp@192.168.99.99
Last login: Sun Jun 8 16:43:56 2025 from 192.168.98.99
Oracle Solaris 11.4.81.195.2
jmoekamp@testbed:~$Using OTP for password-less authentication as well
However it’s possible to have OTP and public key authentication active, so you need a second factor even when you are using public key authentication (For example when you forgot to lock your desktop or your notebook and the credentials of your notebook have been stolen or otherwise compromised)
root@testbed:~# echo "AuthenticationMethods publickey,keyboard-interactive password,keyboard-interactive" > /etc/ssh/sshd_config.d/otp.conf
root@testbed:~# svcadm restart sshLet’s try it again.
joergmoellenkamp@Mac ~ % ssh jmoekamp@192.168.99.99
(jmoekamp@192.168.99.99) OTP code:
Last login: Sun Jun 8 16:48:20 2025 from 192.168.98.99
Oracle Solaris 11.4.81.195.2
jmoekamp@testbed:~$ No login prompt, but the system is asking for an OTP code.